
Unit 42 MDR XSIAM
Unit 42: A Leader in MDR, Again
Click here to jump to more pricing!
Please Note: All Prices are Inclusive of GST
Overview:
A Service Delivered by Palo Alto Networks World-Renowned Unit 42
Unit 42® experts work for you to detect and respond to cyberattacks 24/7, allowing your team to scale fast and focus on what matters most. We use Cortex XDR® so our analysts have unmatched visibility into all data sources (endpoint, network, cloud, and identity) to quickly identify and stop malicious activity most likely to impact your organization:
- Built on Cortex XDR.
- Backed by Unit 42 expertise.
- Enriched with world-class threat intelligence.
The threat landscape is shifting to advanced, multistep attacks. Without constant coverage, proactive hunting, and immediate response, you may not stop these attacks before it’s too late.
Threat actors and their tactics change daily, and many organizations lack broad visibility to interpret and recognize attack indicators.
Overwhelmed by too many low-fidelity alerts, many security teams don’t have additional time for threat hunting.
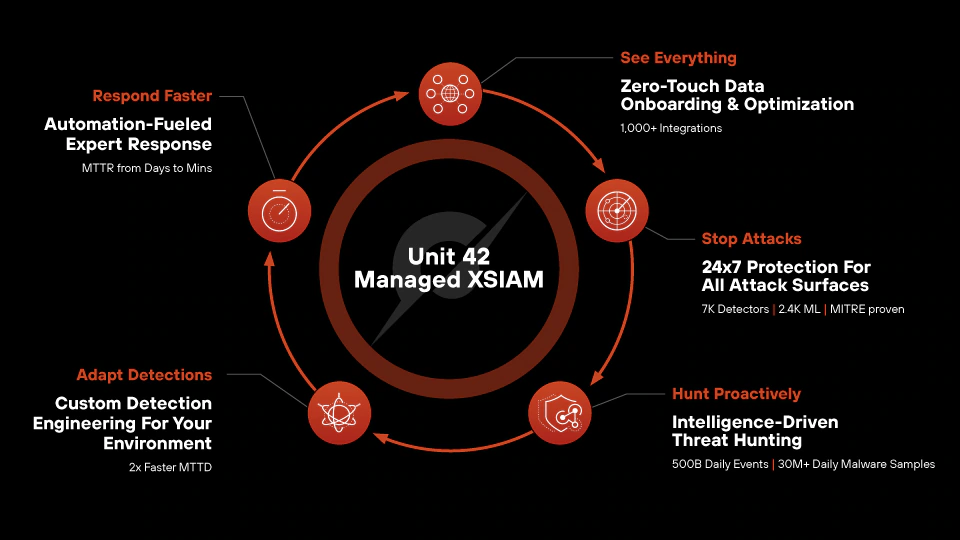
Why Choose Unit 42 Managed XSIAM?
See Everything: Zero-Touch Data Onboarding and MaintenanceAttain holistic visibility across 1K+ native and third-party integrations with zero-touch data onboarding. Unit 42 continuously handles ingestion, mapping and maintenance, enabling security teams to stay focused on proactive defense rather than administrative overhead, for a truly unified SOC vantage point.
Stop Attacks: 24/7 Protection for All Attack SurfacesUnit 42 counters adversaries across endpoints, cloud, network and identity using thousands of dynamic detectors and AI models, ensuring real-time identification and containment of threats. No domain is overlooked, delivering always-on protection against modern attacks.
Hunt Proactively: Intelligence-Driven Threat HuntingDrawing on 500B+ daily events and 30M+ daily malware samples, Unit 42’s elite hunters pinpoint emerging tactics early. Intelligence from thousands of incidents refines detection logic to reduce attacker dwell time, ensuring threats are found before they evolve into major breaches.
Adapt Detections: Custom Detection Engineering for Your EnvironmentWhen new threats arise, Unit 42 rapidly crafts custom detectors that expand beyond built-in XSIAM protections, achieving up to 2X faster mean time to detect. This agile approach turns minor alerts into immediate action items, preventing hidden attackers from escalating damage.
Respond Faster: Automation-Fueled Expert ResponseUnit 42 deploys advanced, automation-first playbooks across your ecosystem, slashing median time to response from days to mere minutes. By containing critical incidents instantly, your security operation gains valuable breathing room to focus on proactive measures rather than emergency triage.
Unit 42 Service Features
Continuous Monitoring- Comprehensive visibility: Cover endpoints, network, cloud, and identity data with SLO-driven, 24/7 monitoring and analysis of security incidents identified in Cortex XDR.
- Alert management and incident triage: Automated and manual review to analyze alert details, incidents, and generate BIoC or IoC rules to understand context and follow-up actions.
- Notification and security event escalation: Escalation of incidents that require attention, leveraging built-in logic and alert stitching aligned with the MITRE ATT&CK® framework.
- Hunting for advanced threats: Sophisticated threat hunting based on analysis of suspicious signals, Cortex XDR analytics, custom detection rules, and Unit 42 research to identify and stop new threats.
- High-fidelity threat intel: Integration of industryleading, comprehensive Unit 42 Threat Intelligence based on telemetry and detections from Palo Alto Networks products across our global customer base to inform and enrich investigations.
- Actionable reporting: Threat reports detailing the scope, source, and attack tools of threats, along with recommended actions; impact of emerging threats affecting multiple organizations to stay ahead of high-profile cyberattack
- Contain threats quickly: Analysts will quickly contain active threats by isolating endpoints and removing malicious files or processes using Cortex XDR.
- Streamlined investigations: Investigate endpoints, analyze forensic artifacts, and network and cloud telemetry to identify incident root cause and scope.
- Recover rapidly: Use of Cortex XDR to remove malicious files, registry keys, and restore damaged files
- Health checks: Identify gaps in hardening requirements with endpoint security profiles, device control, host firewall, and disk encryption
- Vulnerability assessments: Identify and quantify security vulnerabilities (CVEs) for applications installed on your endpoints.
- Host inventory: Review the inventory of hosts to quickly identify any IT or security issues.
Documentation:
Download the Unit 42 MDR XSIAM Datasheet (PDF).
Pricing Notes:
- All Prices are Inclusive of GST
- Pricing and product availability subject to change without notice.
