Call a Specialist Today! (02) 9388 1741
-
Products
- Network Security
- Next Generation Firewalls
-
PA Series Firewalls
- Compare Models
- PA-220R
- PA-410
- PA-415
- PA-415-5G
- PA-440
- PA-450
- PA-450R
- PA-455
- PA-460
- PA-505
- PA-510
- PA-520
- PA-540
- PA-545-POE
- PA-550
- PA-555-POE
- PA-560
- PA-5540
- PA-5560
- PA-5570
- PA-5580
- PA-410R-5G
- PA-450R-5G
- PA-455-5G
- PA-820
- PA-850
- PA-1410
- PA-1420
- PA-3220
- PA-3250
- PA-3260
- PA-3410
- PA-3420
- PA-3430
- PA-3440
- PA-5220
- PA-5250
- PA-5260
- PA-5280
- PA-5410
- PA-5420
- PA-5430
- PA-5450
- PA-7050
- PA-7080
- PA-7500
- VM Series Virtualized Firewalls
-
PA Series Firewalls
- Management (Panorama)
- Cloud Delivered Networking & Security
- SASE
- Prisma Access
- Prisma SD-WAN Hardware
- Prisma SD-WAN Software
- SD Wan Security Services
- AI-Driven Security Operations Platform
- Cortex XDR
- Cortex XSOAR
- Cortex Data Lake
- Autofocus
- Cortex-Xpanse
- Cortex-XSIAM
- Cortex AgentiX
- Cortex Exposure Management
- Cortex Advanced Email Security
- Unit 42
- Cloud Security
- Cloud Delivered Security Services
- Strata Cloud Manager
- Cortex Cloud
- Code to Code Platform
- Prisma Cloud
- Prisma Access
- Prisma Access Browser
- Prisma AIRS
- Prisma SD-WAN
- Prisma Cloud CoPilot
- Services
- Unit 42 Services
-
Unit 42 Services – Assess & Test Your Security Controls
- AI Security Assessment
- Attack Surface Assessment
- Breach Readiness Review
- BEC Readiness Assessment
- Cloud Security Assessment
- Compromise Assessment
- Cyber Risk Assessment
- M&A Cyber Due Diligence
- Penetration Testing
- Purple Team Exercises
- Ransomware Readiness Assessment
- SOC Assessment
- Supply Chain Risk Assessment
- Tabletop Exercises
- Unit 42 Retainer
- Unit 42 Managed XSIAM
- IR Plan Development and Review
- Security Program Design
- Virtual CISO
- Zero Trust Advisory
- Cloud Incident Response
- Digital Forensics
- Incident Response
- Managed Detection and Response
- Managed Threat Hunting
- Managed XSIAM
- Other Products
- Cloud-Enabled Mobile Workforce
- CyberArk
- Chronosphere
- TRAPS/Enpoint Protection
- Rackmount Kits
- Open Source Data Collection
- Control Plane
- Scalable and Reliable Data Store
- Lens
- Differential Diagnosis
- Chronosphere SLOs
- Telemetry Pipeline
- Fluent Bit
- SIEM Log Routing
- View All Products
- Services
- Solutions
- Resources
- Marketplace
- For Gov
- Get a Quote!
- Contact Us
Quantum-safe AI-driven. Every Cloud
Fearlessly innovate across clouds with security that’s a step ahead.
Contact USUSE CASES
Unify policy management, improve performance and secure every edge with PAN-OS.
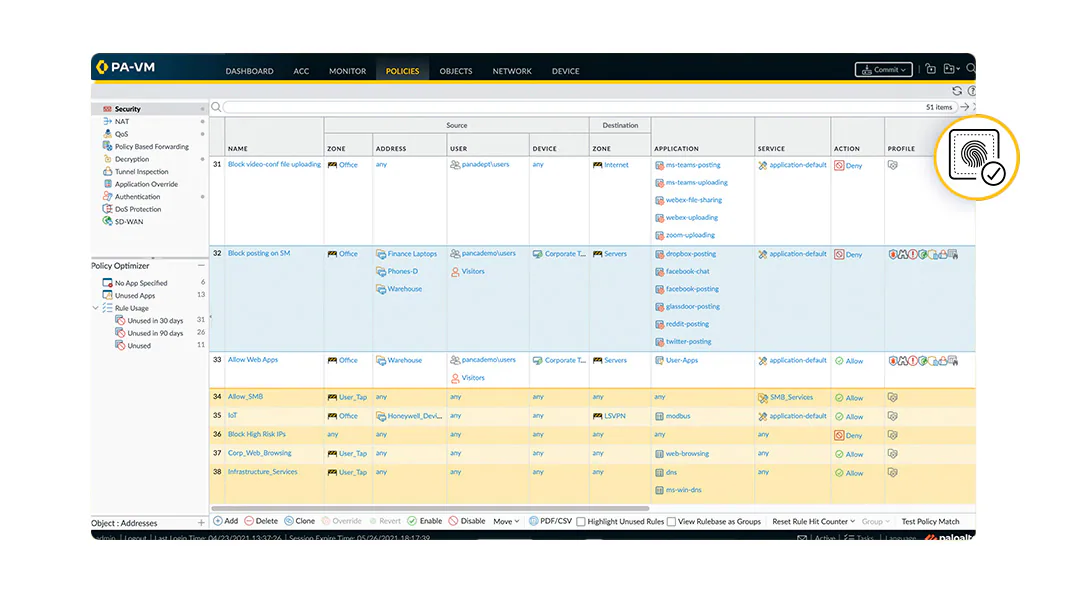
Know your app traffic
PAN-OS® includes App-ID™, our patented traffic classification technology. It automatically discovers and controls new applications — even those that try to evade detection by masquerading as legitimate traffic, hopping ports or sneaking through firewalls under encryption. Plus, our latest post-Quantum cryptographic algorithms prohibit nonsanctioned activity, using vulnerability signatures and threat reporting.
Learn More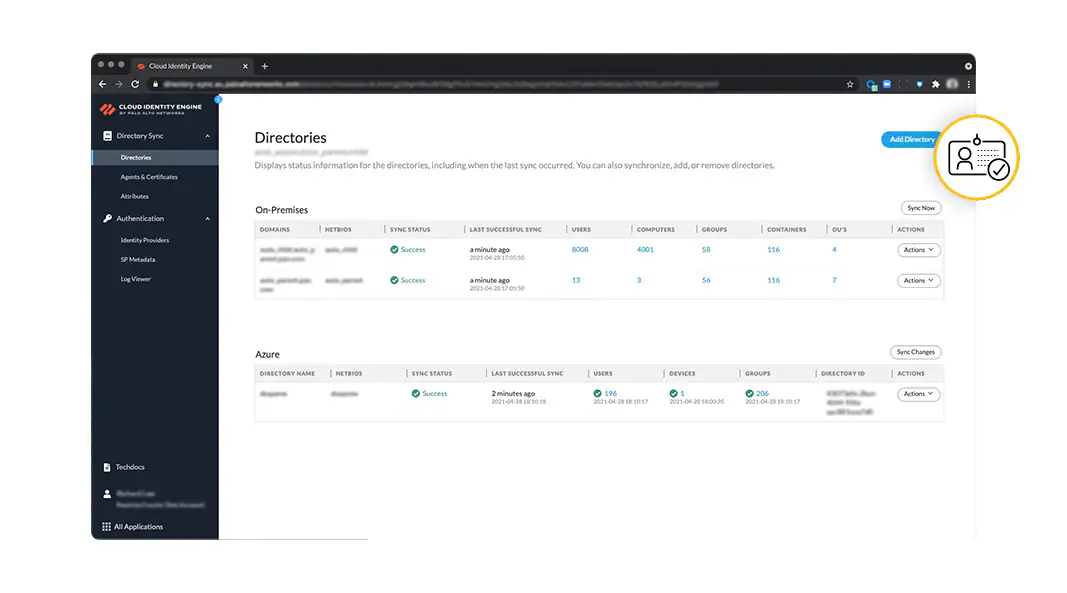
Manage user access
Safeguard your data with PAN-OS post-Quantum VPNs that are based on open standards. Cloud Identity Engine also helps aggregate and synchronize user information across identity providers, allowing consistent authentication and authorization of users, regardless of location and where user identity stores reside. This is all done with point-and-click configuration that automatically synchronizes identity across all identity providers.
Learn More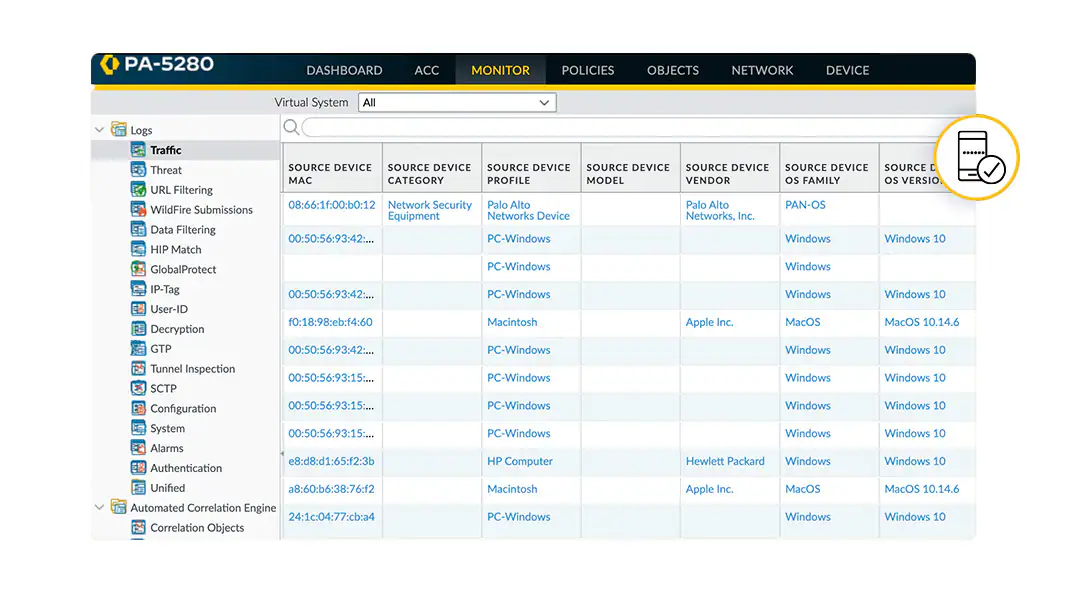
Create device-based rules
Device-ID™, a feature of PAN-OS, provides policy rules for devices regardless of changes to IP address or location. Gain context for how events relate to devices and device policies. PAN-OS can help improve security, decryption, QoS and authentication policies.
Learn More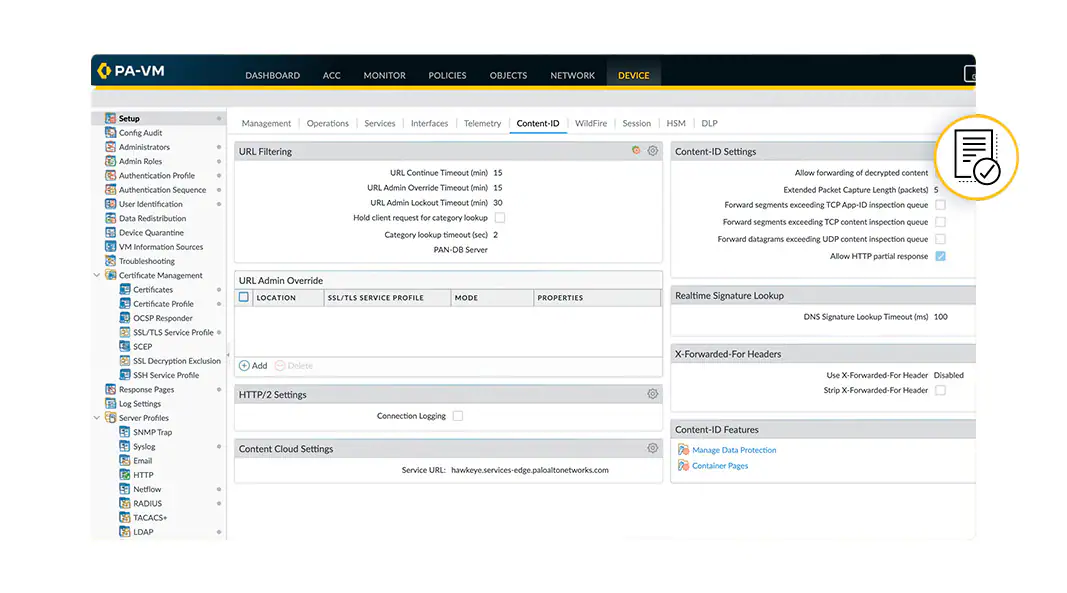
Scan traffic content
Similar to Device-ID and App-ID, Content-ID™ gives you the power to understand and control the content of traffic moving through your network. Content-ID provides comprehensive threat protection in a single scan of network traffic, optimizing your NGFW performance.
Learn More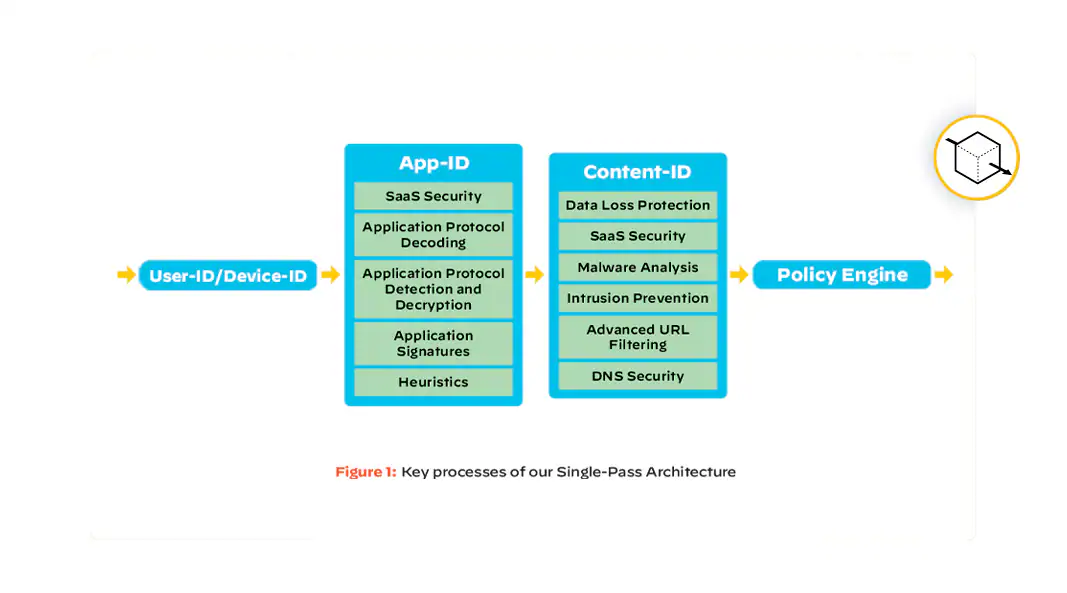
Maximize throughput
The traditional strategy of simply adding more and more security features results in performance degradation and increased latency. Our single-pass architecture performs all necessary security functions in a single scan, reducing complexity and minimizing total cost of ownership.
Learn More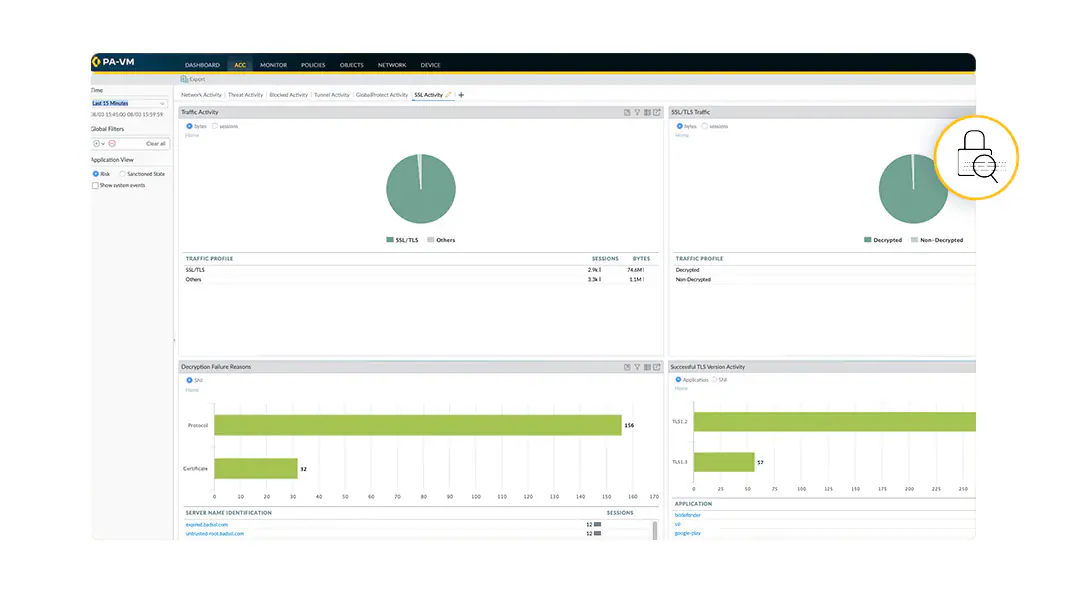
Secure encrypted traffic
Unless inspected, encrypted traffic leaves organizations blind to security risks hidden inside. Hackers take advantage of this lack of visibility to deliver malware within encrypted traffic. PAN-OS provides comprehensive decryption for TLS and SSL encrypted traffic, including TLS 1.3 and HTTP/2.
Learn More
Future proof VPN
Unless inspected, encrypted traffic leaves organizations blind to security risks hidden inside. Hackers take advantage of this lack of visibility to deliver malware within encrypted traffic. PAN-OS provides comprehensive decryption for TLS and SSL encrypted traffic, including TLS 1.3 and HTTP/2.
Learn More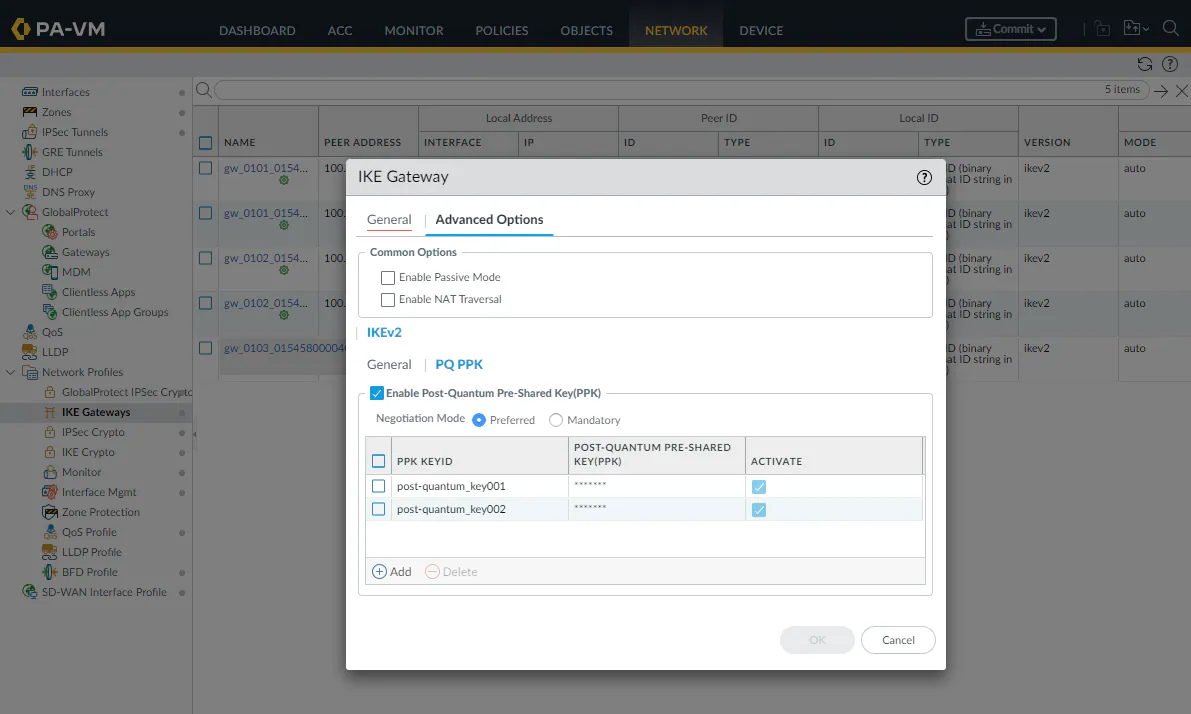
Native web proxy support
Consolidate firewall and proxy into a single platform while managing capabilities through a centralized management platform to build policies. Support explicit proxy through PAC files and also transparent proxy.
Learn MoreEnable identity-based controls in a cloud-first world
Intelligent security, proven ROI
Benefit from efficiency gains, reduced likelihood of data breaches, lower licensing costs and enhanced security.
