What Unit 42 Do?
Intelligence driven, response ready
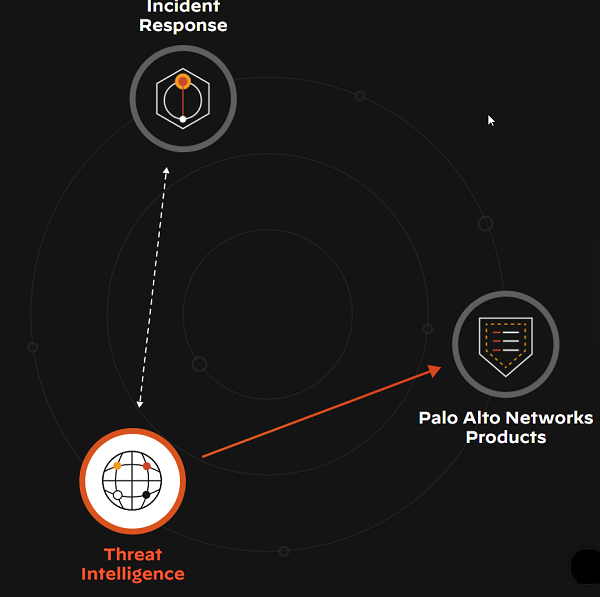
Since 2014, the security community has relied on the Unit 42 Threat Intelligence team to stay ahead of adversaries. It’s the foundation of everything we do.
- Incident Response and Security Consulting
We help security leaders proactively manage cyber risk and respond to over 1,000 incidents a year, leveraging our threat intel to fully eradicate the threat. - Palo Alto Networks Products
We use Palo Alto Networks best-in-class technology to respond to complex incidents while strengthening those same products with our integrated threat intelligence. - Threat Intelligence
The security research we're known for puts threats into context, aiding our customers, products, services and the security community to defend against cyberattacks.
Unit 42 Managed Detectionand Response Service (MDR)
With our team of security experts, we’ll detect and respond to cyberattacks whenever they occur. By bringing us in, your team can scale and focus on what matters most. Our analysts have extensive experience in quickly identifying and stopping the malicious activity most likely to impact your organization.

Why Unit 42?
Intelligence driven. Response ready.
As the threat landscape changes and attack surfaces expand, security strategies must evolve. Our world-renowned incident response team and security consulting experts will guide you before, during and after an incident with an intelligence-driven approach.
Assess your security controls
Proactively assess and test your controls against real-world threats targeting your organization, then communicate your security risk posture to your board and key stakeholders.
Services:
Compromise Assessment
Discover potential compromises, understand the impact and get mitigation recommendations by engaging with our experts. Our threat-informed approach finds historical and ongoing indicators of compromise so you can respond before any further damage occurs.
Ransomware Readiness Assessment
Defending against ransomware attacks starts with having a plan. The Unit 42™ Ransomware Readiness Assessment focuses on preparing you to better prevent, detect, respond to and recover from ransomware.
Cyber Risk Assessment
Define the current state and target state of your security maturity, identify risks and gaps. Make more informed decisions by conducting a framework-based or regulatory-focused (NIST, CIS, ISO, HIPAA, etc.) risk assessment.
Penetration Testing
Can help you simulate real-world attack scenarios that are unique to your organization’s needs in order to test your detection and response capabilities and identify existing vulnerabilities in your environment before an incident occurs.
Tabletop Exercises (TTX)
Up-level your organization’s ability to effectively detect and prevent cyberthreats by collaborating with Unit 42’s offensive security engineers to strategically orchestrate security testing in parallel with network monitoring and incident response processes.
Purple Team Exercises
A cyberattack can result in devastating financial costs, loss of intellectual property and a tarnished reputation. Being prepared to respond can mitigate these risks.
Breach Readiness Review
A cyberattack can result in devastating financial costs, loss of intellectual property and a tarnished reputation. Being prepared to respond can mitigate these risks.
M&A Cyber Due Diligence
Mitigate the inherent security risk of mergers and acquisitions by conducting an independent assessment of the overall information security program currently in place at your M&A candidate.
Supply Chain Risk Assessment
Assess your cybersecurity supply chain risk management strategy, capabilities and controls. Minimize the threat of vendor-based supply chain attacks that could disrupt your business and put your reputation at risk.
Attack Surface Assessment
Manage exposure, reduce risk and improve your security posture by understanding your external attack surface through the eyes of an attacker. This point-in-time assessment gives you visibility into your internet-connected assets, with prioritized recommendations to better defend your organization.
Business Email Compromise
Protecting your organization against business email compromise starts with ensuring you have the right people, process, and controls in place and tuned to defend against BEC and other email-based attacks.
Transform your security strategy
Improve your business resilience with a threat-informed approach to breach preparedness and tighter alignment across your people, processes, technology and governance.
Services:
Security Program Design
Defend your organization from a position of strength by designing a modern security program customized to your unique needs and specific threat profile.
Incident Response Plan Development and Review
Minimize the damage of a cyberattack with a battle-tested incident response plan informed by experts on the frontlines.
Expert Threat Briefing
Transform your security program with a threat-informed approach. Learn about threats targeting your organization with this customized briefing of the threat landscape or a deep dive into a specific threat, like ransomware, focused on your industry, geography or organization size.
Virtual Chief Information Security Officer (vCISO)
Engage a CISO on an interim or part-time basis to identify cyber risk and enhance your security program. You can also leverage these proven leaders after a breach to coordinate your cybersecurity response and communicate with your customers, legal and regulators.
Respond in record time
Deploy Unit 42 incident response experts to quickly investigate, eradicate and remediate even the most advanced attacks, working in partnership with your cyber insurance carrier and legal teams.
Services:
Incident Response
Unit 42 incident response experts are available 24/7 to help you quickly investigate critical security incidents and eradicate threats so that you can recover and get back to business fast.
Cloud Incident Response
Accelerate your investigation, response and recovery. As cloud adoption grows, even simple mistakes lead to outsized impact. With Unit 42, you will take advantage of digital forensics and reponse methods specifically designed for cloud-based incidents.
Digital Forensics
Uncover what happened on your computer systems, network and mobile devices to aid in criminal, fraud, counterintelligence or corporate investigations.
Expert Malware Analysis
Experts give you a complete picture of the threat you face and what you can do to remediate it. This knowledge is crucial in a world where sophisticated malware is often designed to evade sandboxes and automated tools.
Managed Detection and Response (MDR)
With our team of security experts, we’ll detect and respond to cyberattacks whenever they occur. By bringing us in, your team can scale and focus on what matters most. Our analysts have extensive experience in quickly identifying and stopping the malicious activity most likely to impact your organization.
Managed Threat Hunting
Adversaries continually find new ways to compromise systems while staying under the radar. You need to stop them before serious damage occurs. The Unit 42 Managed Threat Hunting service helps you proactively uncover attackers wherever they hide in your infrastructure.
What Sets Us Apart
World-renowned security experts, always in your corner
As threats escalate, we act as your cybersecurity partner to advise and strengthen your security strategies. Our team of incident responders, security consultants and threat researchers help you prepare for and respond to the most challenging threats.
200+
Threat Researchers
Our team is made up of threat analysts, threat hunters, and experts in reverse engineering, malware analysis, and threat modeling. Together, they inform our incident response and cyber risk management services to keep you ahead of the changing threat landscape.
1k+
Incident Response Engagements a Year
With their experience, expertise and unique tooling, our Incident Response and Digital Forensics Services can help your team respond in record time.
30M
Malware Samples Per Day Analyzed
Our 10+ years of historical malware analysis – growing by over 30 million samples per day – help us stay ahead of adversaries and better protect you.
