
Palo Alto Networks Enterprise Firewall PA-7050
High Speed Internet Gateway Deployments within Enterprise
Environments

Our Price: Request a Quote
Our Price: Request a Quote
Click here to jump to more pricing!
Please Note: All Prices are Inclusive of GST
Overview:
The PA-7050 protects datacenters and high-speed networks with firewall throughput of up to 120 Gbps and, fullthreat prevention at speeds of up to 100 Gbps. To address the computationally intensive nature of full-stack classification and analysis at speeds of 120 Gbps, more than 400 processors are distributed across networking, security, switch managementand logging functions. The result is that the PA-7050 allows you to deploy next-generation security in your datacenters without compromising performance.
Classify all applications, on all port, all the time with App-ID.
- Identify the application, regardless of port, encryption (SSL or SSH) or evasive technique employed.
- Use the application, not the port, as the basis for all safe enablement policy decisions: allow, deny, schedule, inspect, apply traffic shaping.
- Categorize unidentified applications for policy control, threat forensics, custom App-ID creation, or packet capture for App-ID development.
Extend safe application enablement policies to any user, at any location, with User-ID and GlobalProtect.
- Agentless integration with Active Directory, LDAP, eDirectory Citrix and Microsoft Terminal Services.
- Easily integrate firewall policies with NAC, 802.1X wireless, Proxies and NAC solutions.
- Deploy consistent policies to local and remote users running Microsoft Windows, Mac OS X, Linux, Android or iOS platforms.
Protect against all threat-both known and unknown-with Content-ID and Wildfire
- Block a range of known threats including exploits, malware and spyware, across all ports, regardless of common threat evasion tactics employed.
- Limit unauthorised transfer of files and sensitive data, and control non-workrelated web surfing.
- Identify unknown malware, analyze for more than 100 malicious behaviors, automatically create and deliver a signature in the next available update.
Delivering Linear Scalability and Performance
The PA-7050 achieves predictable datacenter level protection and performance by applying more than 400 function-specific processors distributed across the following chassis subsystems:
- Network Processing Card (NPC): Each NPC delivers 20 Gbps of firewall performance using multi-core security optimized processors, along with dedicated high-speed networking and content inspection processors. Up to six NPCs, each with 24 traffic interfaces are supported in the PA-7050.
-
Switch Management Card (SMC): The SMC is comprised of three
elements that are key to delivering predictable datacenter
protection and performance: the First Packet Processor, the
1.2 Tbps switch fabric and the management subsystem.
- First Packet Processor (FPP): The FPP utilizes dedicated processing to apply intelligence to the incoming traffic, directing it to the appropriate processing resource to maximize throughput efficiency.
- High Speed Switch Fabric: The 1.2 Tbps switch fabric means that each NPC has access to approximately 100 Gbps of traffic capacity, ensuring that performance and capacity will scale in a linear manner as NPCs are added to the PA-7050.
- Management Subsystem: Unified point of contact for managing all aspects of the PA-7050.
- Log Processing Card (LPC): The LPC uses multi-core processors and 2TB of RAID 1 storage to offload the logging related activities without impacting the processing required for other management related tasks. The LPC allows you to generate on-system queries and reports from the most recent logs collected or forward them to a syslog server for archiving or additional analysis.
The PA-7050 delivers performance and scalability by intelligently applying all available networking and security processing power to application layer traffic classification and threat protection tasks. Orchestrating this ballet of session management tasks is the First Packet Processor which constantly tracks the shared pool of processing and I/O resources across all of the NPCs. When the FPP determines that additional processing resources are available, traffic is intelligently directed across the high-speed switch fabric to that location, even if it resides on a separate NPC. The FPP is the key to delivering linear scalability to the PA-7050, working in conjunction with each of the network processors on the NPCs to utilize all of the available computing resources as a single, cohesive system. This means that as NPCs are added, no traffic engineering changes are required in order to utilize the added capacity.
The controlling element of the PA-7050 is PAN-OSTM, a securityspecific operating system that natively classifies all traffic, inclusive of applications, threats and content, then ties that traffic to the user, regardless of location or device type. The application, content, and user-the elements that run your business-are then used as the basis of your security policies, resulting in an improved security posture and a reduction in incident response time. All traffic classification, content inspection, policy lookup and execution are performed in a single pass. The single pass software architecture, when combined with the processing power of the PA-7050, ensures that you achieve predictable throughput.
Features:
Security Features
-
Application Visibility
Port numbers, protocols, and IP addresses are useful for network devices, but they tell you nothing about what is on your network. Detailed information about the applications, users, and content traversing your network empowers you to quickly determine any risks they pose and quickly respond. Leveraging the rich context provided by Palo Alto Networks firewalls, our visualization, analysis, and reporting tools let you quickly learn more about activity on your network and analyze incidents from a current or comparative perspective. -
User Visibility - An integral component for
secure application enablement policies.
Traditionally, security policies were applied based on IP addresses, but the increasingly dynamic nature of users and applications mean that IP addresses alone have become ineffective as a policy control element for safe application enablement. Our next-generation firewalls integrate with a wide range of enterprise directories and terminal services offerings, allowing you to:- See who is using the applications on your network
- Set policy based on users
- Perform forensic analysis and generate reports on user activities
-
AntiVirus - Network-based Malware
Protection.
The broadening use of social media, messaging and other non-work related applications introduce a variety of vectors for viruses, spyware, worms and other types of malware. Palo Alto Networks next-generation firewalls allow you to block unwanted applications with App-ID, and then scan allowed applications for malware. -
IPS
Today's attacks on your network use a combination of application vectors and exploits. Palo Alto Networks next-generation firewalls arm you with a two-pronged approach to stopping these attacks. Unwanted applications are blocked through App-ID, and the applications you choose to allow through are scanned for vulnerability exploits by our NSS-approved IPS engine. -
Data Filtering & File Blocking
The application function level control, file blocking by type, and data filtering features of our next-generation firewalls allow you to implement a range of policies that help balance permitting the use of personal or non-work related applications, with the business and security risks of unauthorised file and data transfer. -
Modern Malware Protection - WildFire:
Protection from targeted and unknown threats.
Modern attackers are increasingly using targeted and new unknown variants of malware to sneak past traditional security solutions. To address this, Palo Alto Networks developed WildFire, which identifies new malware in minutes. By executing suspect files in a virtual environment and observing their behavior, Palo Alto Networks identifies malware quickly and accurately, even if the malware sample has never been seen before. Once a file is deemed malicious, WildFire automatically generates protections that are delivered to all WildFire subscribers within an hour of detection. A WildFire license provides your IT team with a wealth of forensics to see exactly who was targeted, the application used in the delivery, and any URLs that were part of the attack. -
URL Filtering - Control Web Activity with URL
Filtering.
The perfect complement to the policy-based application control provided by App-ID is our on-box URL filtering database, which gives you total control over related web activity. By addressing your lack of visibility and control from both an application and web perspective, App-ID and URL Filtering together protect you from a full spectrum of legal, regulatory, productivity, and resource utilization risks. -
Mobile Security
Mobile computing is one of the most disruptive forces in information technology. It is revolutionizing how and where employees work, as well as the tools they use to perform their jobs. Mobile devices are not just ways to access existing applications such as corporate email, but the platform for opening up entirely new ways of doing business. Make sure that you have the proper security to extend your business applications and data to smartphones, tablets and laptops. Learn how to safely enable mobile devices by using GlobalProtect from Palo Alto Networks.
Networking Features
-
Decryption - Identify & Control Encrypted
Traffic.
Take control of your SSL and SSH encrypted traffic and ensure it is not being used to conceal unwanted activity or dangerous content. Using policy-based decryption and inspection, you can confirm that SSL and SSH are being used for business purposes only, instead of to spread threats or unauthorised data transfer. -
IPv6 - Safely enabling applications, users
and content in IPv6 environments.
Our next-generation firewalls allow you to deploy consistent, safe application enablement policies across IPv6, IPv4 and mixed environments. -
Networking
Our flexible networking architecture includes dynamic routing, switching, and VPN connectivity, which enables you to easily deploy Palo Alto Networks next-generation firewalls into nearly any networking environment. -
VPN - Standards-based VPN Connectivity.
Secure site-to-site and remote user connectivity is a critical infrastructure component. Every Palo Alto Networks next-generation firewall platform allows you to easily and securely communicate between sites using standards-based IPSec VPN connections. Remote user communications are protected through a rich set of VPN features. -
Virtualization Security
The VM-Series supports the exact same next-generation firewall and advanced threat prevention features available in our physical form factor appliances, allowing you to safely enable applications flowing into, and across your private, public and hybrid cloud computing environments. Automation features and an API enable you to dynamically update security policies as your VM environment changes, eliminating potential security lag. The VM-Series supports the following hypervisors: VMWare ESXi and NSX, Citrix SDX, KVM (Centos/RHEL), Ubuntu, Amazon Web Services.
Management Features
-
Centralized Management
The centralized management features in Panorama will minimize the administrative efforts and operational costs associated with your deployment of our next-generation firewalls in multiple locations - either internally or globally. Panorama allows your team to centrally manage all device aspects including configuration and policy deployment, visibility into applications, users and content as well as logging and reporting. -
Device Management
Our firewall management philosophy is to make administrative tasks such as report generation, log queries, policy creation, and ACC browsing easy to execute and consistent, no matter which mechanism - web interface, Panorama, CLI or API - you use. -
Policy Control - Secure Application
Enablement.
The increased visibility into applications, users and content delivered by Palo Alto Networks simplifies figuring out which applications are traversing your network, who is using them, and the potential security risks. Armed with this data, you can apply secure enablement policies with a range of responses that are more finely tuned than the traditional 'allow or deny' approach. -
Redundancy
Palo Alto Networks next-generation firewalls support a series of redundancy and resiliency features that ensure your firewall will continue to provide the secure application enablement you need to keep your business running. -
Virtual Systems - Scalable Firewall Services
With Virtual Systems.
Virtual systems are unique and distinct next-generation firewall instances within a single Palo Alto Networks firewall. Instead of deploying many individual firewalls, security service providers and enterprises can deploy a single pair of firewalls (high availability) and enable a series of virtual firewall instances (virtual systems). Each virtual system is an independent (virtual) firewall within your firewall that is managed separately and cannot be accessed or viewed by other users.
Next-Generation Firewall Overview:
Fundamental shifts in the application and threat landscape, user behavior, and network infrastructure have steadily eroded the security that traditional port-based firewalls once provided. Your users are accessing all types of applications using a range of device types, often times to get their job done. Meanwhile, datacenter expansion, virtualization, mobility, and cloud-based initiatives are forcing you to re-think how to enable application access yet protect your network.
Traditional responses include an attempt to lock down all application traffic through an evergrowing list of point technologies in addition to the firewall, which may hinder your business; or allowing all applications, which is equally unacceptable due to increased business and security risks. The challenge that you face is that your traditional port-based firewall, even with bolt-on application blocking, does not provide an alternative to either approach. In order to strike a balance between allowing everything and denying everything, you need to safely enable applications by using business-relevant elements such as the application identity, who is using the application, and the type of content as key firewall security policy criteria.
Key safe enablement requirements:
- Identify applications, not ports. Classify traffic, as soon as it hits the firewall, to determine the application identity, irrespective of protocol, encryption, or evasive tactic. Then use that identity as the basis for all security policies.
- Tie application usage to user identity, not IP address, regardless of location or device. Employ user and group information from enterprise directories and other user stores to deploy consistent enablement policies for all your users, regardless of location or device.
- Protest against all threats-both known and unknown. Prevent known vulnerability exploits, malware, spyware, malicious URLs while analyzing traffic for, and automatically delivering protection against highly targeted and previously unknown malware.
- Simplify policy management. Safely enable applications and reduce administrative efforts with easy-to-use graphical tools, a unified policy editor, templates, and device groups.
Safe application enablement policies can help you improve your security posture, regardless of the deployment location. At the perimeter, you can reduce your threat footprint by blocking a wide range of unwanted applications and then inspecting the allowed applications for threats- both known and unknown. In the datacenter - traditional or virtualized, application enablement translates to ensuring only datacenter applications are in use by authorised users, protecting the content from threats and addressing security challenges introduced by the dynamic nature of the virtual infrastructure. Your enterprise branch offices and remote users can be protected by the same set of enablement policies deployed at the headquarters location, thereby ensuring policy consistency.
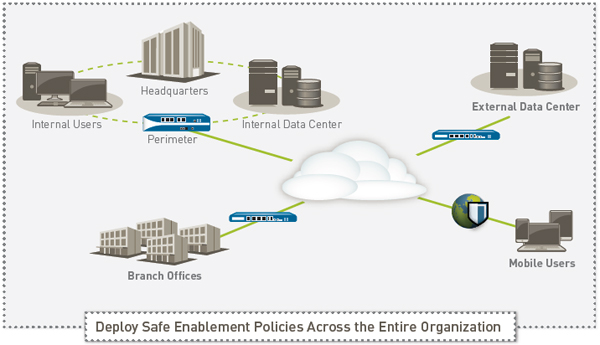
Enabling Applications to Empower the Business
Safe application enablement with Palo Alto Networks™ next-generation firewalls helps you address your business and security risks associated with the rapidly growing number of applications traversing your network. By enabling applications for users or groups of users, both local, mobile, and remote, and protecting the traffic against known and unknown threats, you can improve your security posture while growing your business.
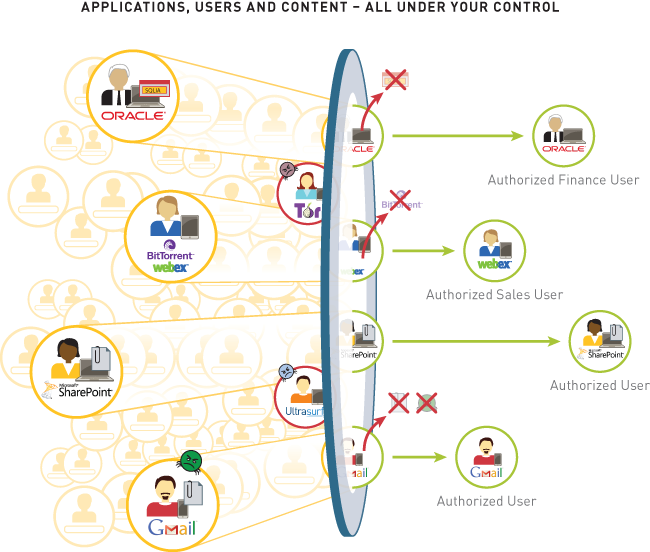
- Classifying all applications, across all ports, all the time. Accurate traffic classification is the heart of any firewall, with the result becoming the basis of the security policy. Today, applications can easily bypass a port-based firewall; hopping ports, using SSL and SSH, sneaking across port 80, or using non-standard ports. App-ID™ addresses the traffic classification visibility limitations that plague traditional firewalls by applying multiple classification mechanisms to the traffic stream, as soon as the firewall sees it, to determine the exact identity of application traversing your network, regardless of port, encryption (SSL or SSH) or evasive technique employed. The knowledge of exactly which applications are traversing your network, not just the port and protocol, becomes the basis for all your security policy decisions. Unidentified applications, typically a small percentage of traffic, yet high in potential risk, are automatically categorized for systematic management- which can include policy control and inspection, threat forensics, creation of a custom App-ID, or a packet capture for Palo Alto Networks App-ID development.
- Integrating users and devices, not just IP addresses into policies. Creating and managing security policies based on the application and the identity of the user, regardless of device or location, is a more effective means of protecting your network than relying solely on port and IP address. Integration with a wide range of enterprise user repositories provides the identity of the Microsoft Windows, Mac OS X, Linux, Android, or iOS user accessing the application. Users who are traveling or working remotely are seamlessly protected with the same, consistent policies that are in use on the local, or corporate network. The combined visibility and control over a user's application activity means you can safely enable the use of Oracle, BitTorrent, or Gmail, or any other application traversing your network, no matter where or how the user is accessing it.
- Protect against all threats, both known and unknown. To protect today's modern network, you must address a blend of known exploits, malware and spyware as well as completely unknown and targeted threats. This process begins by reducing the network attack surface by allowing specific applications and denying all others, either implicitly through a deny-all-else strategy or through explicit policies. Coordinated threat prevention can then be applied to all allowed traffic, blocking known malware sites, vulnerability exploits, viruses, spyware and malicious DNS queries in a single pass. Custom or otherwise unknown malware is actively analyzed and identified by executing the unknown files and directly observing more than 100 malicious behaviors in a virtualized sandbox environment. When new malware is discovered, a signature for the infecting file and related malware traffic is automatically generated and delivered to you. All threat prevention analysis uses full application and protocol context, ensuring that threats are always caught even if they attempt to hide from security in tunnels, compressed content or on non-standard ports.
Deployment and Management Flexibility
Safe application enablement functionality is available in either a purpose-built hardware platform or in a virtualized form factor. When you deploy multiple Palo Alto Networks firewalls, in either hardware or virtual form factors, you can use Panorama, an optional centralized management offering to gain visibility into traffic patterns, deploy policies, generate reports and deliver content updates from a central location.
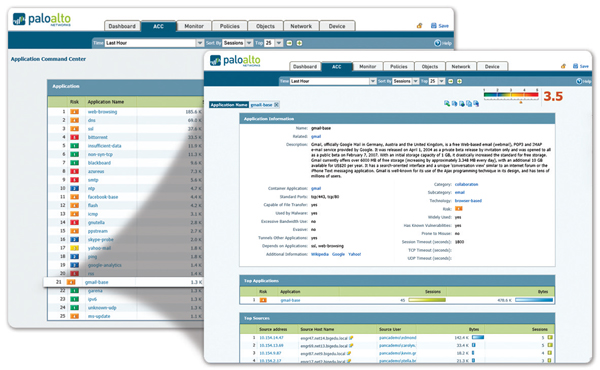
Application Visibility:
View application activity in a clear, easy-to-read format. Add
and remove filters to learn more about the application, its
functions and who is using them.
Safe Application Enablement: A Comprehensive Approach
Safe application requires a comprehensive approach to securing your network and growing your business that begins with in-depth knowledge of the applications on your network; who the user is, regardless of their platform or location; what content, if any, the application is carrying. With more complete knowledge of network activity, you can create more meaningful security policies that are based on elements of application, user and content that are relevant to your business. The user location, their platform and where the policy is deployed-perimeter, traditional or virtualized datacenter, branch office or remote user- make little or no difference to how the policy is created. You can now safely enable any application, any user, and any content.
Complete Knowledge Means Tighter Security Policies
Security best practices dictate that more complete knowledge of what's on your network is beneficial to implementing tighter security policies. For example, knowing exactly which applications are traversing your network, as opposed to the broader set of traffic that is portbased, enables your administrators to specifically allow the applications that enable your business while blocking, unwanted applications. The knowledge of who the user is, not just their IP address, adds another policy criteria that allows you to be more specific in your policy assignment.
- Using a powerful set of graphical visualization tools, your administrators can gain a more complete picture of the application activity, the potential security impact, and make a more informed policy decision. Applications are continuously classified and as their state changes, the graphical summaries are dynamically updated, displaying the information in an easy-touse, web-based interface.
- New or unfamiliar applications can be quickly investigated with a single click that displays a description of the application, its behavioral characteristics, and who is using it.
- Additional visibility into URL categories, threats, and data patterns provides a complete and well-rounded picture of network activity.
- Unknown applications, typically a small percentage on every network, yet high in potential risk, are categorized for analysis to determine if they are internal applications, as yet unidentified commercial applications, or threats.
Enabling Applications and Reducing Risk
Safe application enablement uses policy decision criteria that includes application/application function, users and groups, and content as a means of striking a balance between business limiting denying of all applications and the high risk alternative of allowing all applications.
At the perimeter, including branch offices, mobile, and remote users, enablement policies are focused on identifying all the traffic, then selectively allowing the traffic based on user identity; then scanning the traffic for threats. Policy examples may include:
- Limit the use of webmail and instant messaging usage to a select few variants; decrypt those that use SSL, inspect the traffic for exploits and upload unknown files to WildFire™ for analysis and signature development.
- Allow streaming media applications and websites but apply QoS and malware prevention to limit the impact on VoIP applications and protect your network.
- Control Facebook by allowing all your users to "browse", blocking all Facebook games and social plugins; and allowing Facebook posting only for marketing. Scan all Facebook traffic for malware and exploits
- Control web-surfing by allowing and scanning traffic to business related web sites while blocking access to obvious non-work related web sites; "coach" access to questionable sites through customized block pages.
- Enforce consistant security by transparently deploying the same policies to all users, local, mobile, or remote, with GlobalProtect™.
- Use an implicit deny-all-else strategy or explicitly block unwanted applications such as P2P and circumventors or traffic from specific countries to reduce the application traffic that introduces business and security risk.
In the datacenter-traditional, virtualized or a combination thereof-enablement examples are focused on confirming applications, looking for rogue applications, and protecting the data.
- Isolate the Oracle-based credit card number repository in its own security zone; control access to finance groups, forcing the traffic across its standard ports, and inspecting the traffic for application vulnerabilities.
- Enable only the IT group to access the datacenter using a fixed set of remote management applications (e.g., SSH, RDP, Telnet) across their standard ports.
- Allow Microsoft SharePoint Administration to be used by only your administration team, and allow access to Microsoft SharePoint Documents for all other users.
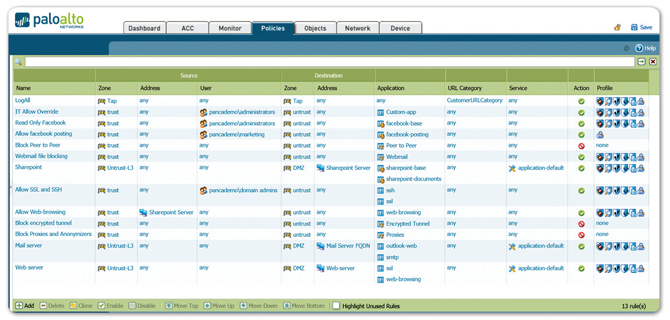
Unified Policy Editor: A familiar look and
feel enables the rapid creation and deployment of policies
that control applications, users and content.
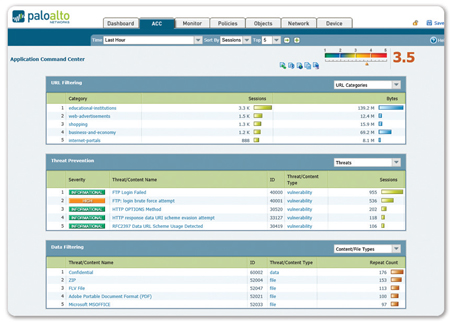
Content and Threat Visibility: View URL,
threat and file/data transfer activity in a clear,
easy-to-read format. Add and remove filters to learn more
about individual elements.
Protecting Enabled Applications
Safe application enablement means allowing access to certain applications, then applying specific policies to block known exploits, malware and spyware - known or unknown; controlling file or data transfer, and web surfing activity. Common threat evasion tactics such as port-hopping and tunneling are addressed by executing threat prevention policies using the application and protocol context generated by the decoders in App-ID. In contrast, UTM solutions take a silo-based approach to threat prevention, with each function, firewall, IPS, AV, URL filtering, all scanning traffic without sharing any context, making them more susceptible to evasive behavior.
- Block Known Threats: IPS and Network Antivirus/Anti-spyware. A uniform signature format and a stream-based scanning engine enables you to protect your network from a broad range of threats. Intrusion prevention system (IPS) features block network and application-layer vulnerability exploits, buffer overflows, DoS attacks, and port scans. Antivirus/Anti-spyware protection blocks millions of malware variants, as well as any malware-generated command-and-control traffic, PDF viruses, and malware hidden within compressed files or web traffic (compressed HTTP/HTTPS). Policy-based SSL decryption across any application on any port protects you against malware moving across SSL encrypted applications.
- Block Unknown, Targeted Malware: Wildfire. Unknown or targeted malware is identified and analyzed by WildFire, which directly executes and observes unknown files in a cloud-based, virtualized sandbox environment. WildFire monitors for more than 100 malicious behaviors and the result is delivered immediately to the administrator in the form of an alert. An optional WildFire subscription offers enhanced protection, logging, and reporting. As a subscriber, you are protected within an hour when a new piece of malware is found anywhere in the world, effectively stopping the spread of new malware before it impacts you. As a subscriber, you also gain access to integrated WildFire logging and reporting and an API for submitting samples to the WildFire cloud for analysis.
- Identify Bot-Infected Hosts. App-ID classifies all applications, across all ports, including any unknown traffic, which can often expose anomalies or threats in your network. The behavioral botnet report correlates unknown traffic, suspicious DNS and URL queries and a variety of unusual network behaviors to reveal devices that are likely infected with malware. The results are displayed in the form of a list of potentially infected hosts that can be investigated as possible members of a botnet.
- Limit Unauthorised File and Data Transfers. Data filtering features enable your administrators to implement policies that will reduce the risks associated with unauthorised file and data transfers. File transfers can be controlled by looking inside the file (as opposed to looking only at the file extension), to determine if the transfer action should be allowed or not. Executable files, typically found in drive-by downloads, can be blocked, thereby protecting your network from unseen malware propagation. Data filtering features can detect, and control the flow of confidential data patterns (credit card or social security numbers as well as custom patterns).
- Control Web Surfing. A fully-integrated, customizable URL filtering engine allows your administrators to apply granular web-browsing policies, complementing application visibility and control policies and safeguarding the enterprise from a full spectrum of legal, regulatory, and productivity risks. In addition, the URL categories can be leveraged into the policies to provide further granularity of control for SSL decryption, QoS, or other rule bases.
Ongoing Management and Analysis
Security best practices dictate that your administrators strike a balance between proactively managing the firewall, whether it is a single device or many hundreds, and being reactive, investigating, analyzing, and reporting on security incidents.
- Management: Each Palo Alto Networks platform can be managed individually via a command line interface (CLI) or full-featured browser-based interface. For large-scale deployments, Panorama can be licensed and deployed as a centralized management solution that enables you to balance global, centralized control with the need for local policy flexibility using features such as templates and shared policy. Additional support for standards-based tools such as SNMP, and REST-based APIs allow you to integrate with third-party management tools. Whether using the device's web interface or Panorama's, the interface look and feel is identical, ensuring that there is no learning curve when moving from one to another. Your administrators can use any of the provided interfaces to make changes at any time without needing to worry about synchronization issues. Role-based administration is supported across all management mediums, allowing you to assign features and functions to specific individuals.
- Reporting: Predefined reports can be used as-is, customized, or grouped together as one report in order to suit the specific requirements. All reports can be exported to CSV or PDF format and can be executed and emailed on a scheduled basis.
- Logging: Real-time log filtering facilitates rapid forensic investigation into every session traversing your network. Log filter results can be exported to a CSV file or sent to a syslog server for offline archival or additional analysis.
Purpose-Built Hardware or Virtualized Platforms
Palo Alto Networks offers a full line of purpose-built hardware platforms that range from the PA-200, designed for enterprise remote offices to the PA-5060, which is designed for high-speed datacenters. The platform architecture is based on a single pass software engine and uses function specific processing for networking, security, threat prevention and management to deliver you predictable performance. The same firewall functionality that is delivered in the hardware platforms is also available in the VM-Series virtual firewall, allowing you to secure your virtualized and cloud-based computing environments using the same policies applied to your perimeter or remote office firewalls.
Technology:
Next-Generation Firewall Technology
The underlying technologies within our next-generation firewall form the basis of an enterprise security platform that natively classifies all traffic, on all ports, inclusive of applications, threats and content. The traffic is then tied to the user, regardless of location or device type allowing you to use the application, content, and user - the core elements that run your business - as the basis of your safe application enablement policies.
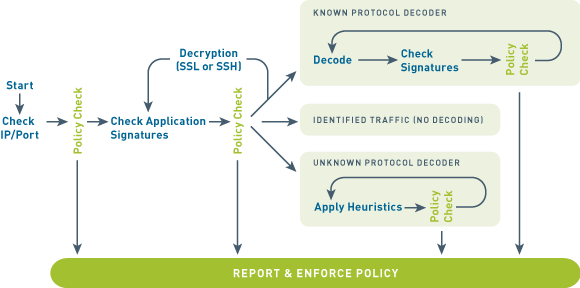
App-ID
Traffic classification is at the heart of any firewall, because your classifications form the basis of your security policies. Traditional firewalls classify traffic by port and protocol. At one point, this was a satisfactory mechanism for securing the perimeter. Not anymore.
If you still use a port-based firewall it is easy for applications to bypass it by:
- Hopping ports
- Using SSL and SSH
- Sneaking across port 80
- Using non-standard ports
Simply put, the traffic classification limitations of port-based firewalls make them unable to protect today's network. That's why we developed App-ID™, a patent-pending traffic classification system only available in Palo Alto Networks firewalls. App-ID™ instantly applies multiple classification mechanisms to your network traffic stream, as soon as the device sees it, to accurately identify applications.
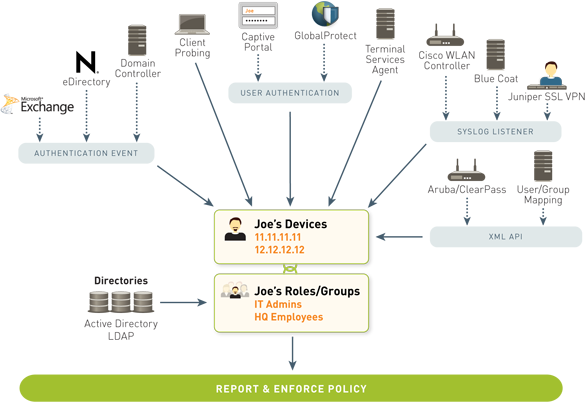
User-ID
User-ID seamlessly integrates Palo Alto Networks next-generation firewalls with a wide range of user repositories and terminal services environments. Depending on your network environment, there are a variety of ways you can map a user's identity to an IP address. Some of these include:
- Authentication events
- User authentication
- Terminal services monitoring
- Client probing
- Directory services integration
- Syslog Listener and a powerful XML API
The user identity, when tied to the application activity, provides you with more complete visibility into usage patterns, greater policy control, and more granular logging, reporting and forensics capabilities.
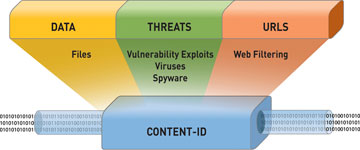
Content-ID
Content-ID gives you a real-time threat prevention engine, combined with a comprehensive URL database, and elements of application identification to:
- Limit unauthorised data and file transfers
- Detect and block exploits, malware and malware communications
- Control unapproved web surfing
The application visibility and control of App-ID, coupled with the content inspection enabled by Content-ID, empowers your IT team to regain control over your application traffic and related content.
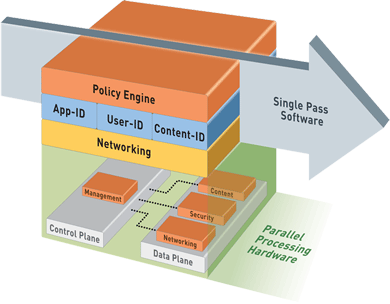
Purpose-built Platform
Multi-Gbps throughput is enabled through function-specific processing for networking, security, threat prevention and management, which are tightly integrated with a single pass software engine to maximize throughput. A 10Gbps data plane smoothes traffic flow between processors while the physical separation of control and data plane ensures that management access is always available, irrespective of traffic load.
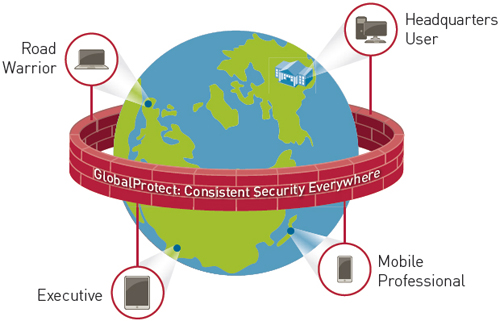
GlobalProtect
GlobalProtect provides a comprehensive security solution for mobile devices built upon the technologies of the Palo Alto Networks enterprise security platform and tailored to address mobile requirements. It delivers unprecedented levels of integration to deliver a unique solution that combines technology, global intelligence and policy enforcement over mobile apps and threats. These principles allow businesses to provide a safe environment for applications and data while still permitting users to enjoy the native user experience of their preferred device.
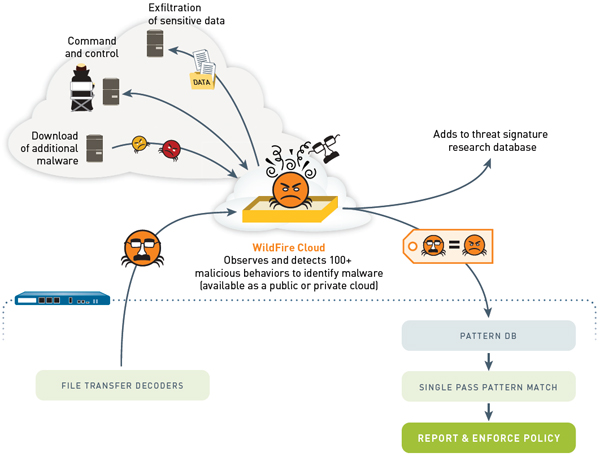
WildFire
WildFireTM simplifies an organization's response to the most dangerous threats-automatically detecting unknown malware and quickly preventing threats before organizations are compromised. Unlike legacy security solutions, WildFire quickly identifies and stops these advanced attacks without requiring manual human intervention or costly Incidence Response (IR) services after the fact.
- Unified hybrid cloud architecture, either deployed through the public cloud, or via a private cloud appliance that maintains all data on the local network.
- Dynamic analysis of suspicious content in a cloud-based virtual environment to discover unknown threats.
- Automatic creation and enforcement of best-in-class content-based malware protections.
- Link detection in email, proactively blocking access to malicious websites.
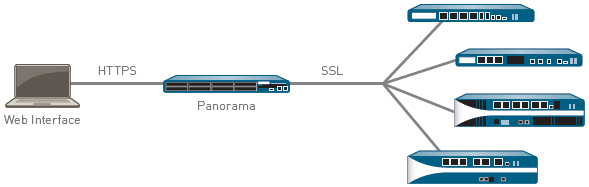
Panorama
Panorama enables you to centrally manage the process of configuring devices, deploying security policies, performing forensic analysis, and generating reports across your entire network of our next-generation firewalls. Available as either a virtual appliance or a dedicated management platform, Panorama and the individual device management interfaces share the same web-based look and feel, ensuring workflow consistency while minimizing any learning curve or delay in executing the task at hand.
Technical Specifications:

| Model | PA-7050 System | PA-7000-20G-NPC |
|---|---|---|

|

|
|
| Performance and Capacities Specifications | ||
| Firewall throughput (App-ID enabled) | 120 Gbps | 20 Gbps |
| Threat prevention throughput (DSRI Enabled2) | 100 Gbps | 16 Gbps |
| Threat prevention throughput | 60 Gbps | 10 Gbps |
| IPSec VPN throughput | 24 Gbps | 4 Gbps |
| New sessions per second | 720,000 | 120,000 |
| Max sessions | 24,000,000 | 4,000,000 |
| Virtual routers | 225 | 225 |
| Virtual systems (base/max3) | 25/225 | N/A |
| Security zones | 900 | 900 |
| Max. number of policies | 40,000 | 40,000 |
| Hardware Specifications | ||
| I/O | (72) 10/100/1000, (48) Gigabit SFP, (24) 10 Gigabit SFP+ | (12) 10/100/1000, (8) Gigabit SFP, (4) 10 Gigabit SFP+ (Each PA-7050 supports up to six NPCs) |
| Management I/O |
((2) 10/100/1000+(2) 40Gbps high availability, (1) 10/100/1000 out-of-band management, (1) RJ45 console port |
|
| Storage Options | 80GB SSD System Drive + 4x1TB HDD on Log Processing Card | |
| Storage Capacity | 2TB RAID1 | |
| Power supply (Avg/max power consumption) | 4x2500W AC (2400W / 2700W) | 4x2500W AC (2400W / 2700W) |
| Max BTU/HR | 9,213 | 9,213 |
| Input Voltage (Input Frequency) | 200-240VAC (50-60Hz) | |
| Max Current Consumption | 12A@240VAC | |
| Max Inrush Current | 200A | |
| Dimensions | 15.75"H x 19"W x 24"D | |
| Weight (Stand alone device/as shipped) | 184Lbs | |
| Safety | UL, CUL, CB | |
| EMI | FCC Class A, CE Class A, VCCI Class A | |
| Certifications | NEBS Level 3 (pending) | |
| Environment | ||
| Operating temperature | 32° to 122° F, 0° to 50° C | |
| Non-operating temperature | -4° to 158° F, -20° to 70° C | |
Networking Specifications:
Interface Modes
Routing
IPV6
IPSEC VPN
|
VLANS
Network Address Translation (NAT):
High-Availability
|
Security Specifications:
Firewall
Wildfire
File and Data Filtering
User Integration (User-ID)
IPSEC VPN (Site-To-Site)
|
Threat Prevention (Subscription Required)
Quality of Service (QOS)
SSL VPN/Remote Access (GlobalProtect)
Management, Reporting, Visibility Tools
|
* Adding virtual systems to the base quantity requires a separately purchased license.
1 Performance and capacities are measured under ideal testing conditions using PAN-OS 6.0.
2 DSRI = Disable Server Response Inspection.
3 Adding virtual systems to the base quantity requires a separately purchased license.
Documentation:
Download the Palo Alto Networks Firewall Overview Datasheet (PDF).
Download the Palo Alto Networks PA-7050 Specification Datasheet (PDF).
Pricing Notes:
- All Prices are Inclusive of GST
- Pricing subject to change without notice.
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Requires PAN-OS 9.0 or higher. Only available as part of a configured system bundle, not sold separately
Our Price: Request a Quote
Requires PAN-OS 9.0 or higher
Our Price: Request a Quote
Requires PAN-OS 8.1.5 or higher, must be paired with PA-7050-FANTRAY-R-A
Our Price: Request a Quote
Requires PAN-OS 8.1.5 or higher, must be paired with PA-7050-FANTRAY-L-A
Our Price: Request a Quote
Our Price: Request a Quote
Necessary accessory for use with PA-7050-DC systems deployed in regions requiring ETSI 300 386 Conducted Emission voltage class A compliance.
Our Price: Request a Quote
Requires PAN-OS 9.0 or higher
Our Price: Request a Quote
Requires PAN-OS 10.0 or higher
Our Price: Request a Quote
Requires PAN-OS 9.0 or higher. Only available as part of a configured system bundle, not sold separately
Our Price: Request a Quote
Requires PAN-OS 9.0 or higher
Our Price: Request a Quote
Our Price: Request a Quote
Formatted boot media, loaded with PAN-OS, 4800G capacity, for use with the 1st generation switch management card (SMC); PAN-PA-7050-SMC, PAN-PA-7050-SMC-SYS, PAN-PA-7080-SMC, PAN-PA-7080-SMC-SYS. NOT FOR USE WITH SMC-B, INCOMPATIBLE WITH PAN-PA-7050-SMC-B and PA-7080-SMC-B
Our Price: Request a Quote
Supports one PA-7000
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5200 Series, PA-3260; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5200 Series, PA-3260; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5200 Series, PA-3260; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5200 Series, PA-3260; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5200 Series, PA-3260; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5250, PA-5260, PA-5280; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5250, PA-5260, PA-5280; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5250, PA-5260, PA-5280; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5250, PA-5260, PA-5280; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5250, PA-5260, PA-5280; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5000 Series, PA-5200 Series, PA-3200 Series, PA-3000 Series, PA-800 Series. PA-220R; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 series, PA-5450 (NC only), PA-5200 Series, PA-5060, PA-5050, PA-3200 Series, PA-3060, PA-850; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 series, PA-5450, PA-5200 Series, PA-5060, PA-5050, PA-3200 Series, PA-3060, PA-850; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 series, PA-5450, PA-5200 Series, PA-5060, PA-5050, PA-3200 Series, PA-3060, PA-850; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5000 Series, PA-5200 Series, PA-3200 Series, PA-3000 Series, PA-800 Series, PA-220R; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5000 Series, PA-5200 Series, PA-3200 Series, PA-3000 Series, PA-800 Series, PA-220R; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5200 Series, PA-3260; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA_5450, PA-5200 Series, PA-3260; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5250, PA-5260, PA-5280; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5250, PA-5260, PA-5280; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5000 Series, PA-5200 Series, PA-3200 Series, PA-3000 Series, PA-800 Series. PA-220R; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 series, PA-5450, PA-5200 Series, PA-5060, PA-5050, PA-3200 Series, PA-3060, PA-850; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 series, PA-5450, PA-5200 Series, PA-5060, PA-5050, PA-3200 Series, PA-3060, PA-850; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5000 Series, PA-5200 Series, PA-3200 Series, PA-3000 Series, PA-800 Series, PA-220R; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5000 Series, PA-5200 Series, PA-3200 Series, PA-3000 Series, PA-800 Series, PA-220R; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5000 Series, PA-5200 Series, PA-3200 Series, PA-3000 Series, PA-800 Series, PA-220R; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7050-SMC-B, PA-7080-SMC-B, PA-7000-100G-NPC-A, PA-7000-20GQXM-NPC, PA-5450 (NC only), PA-5200 Series, PA-5050, PA-5060, PA-3060, PA-850; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 series, PA-5450, PA-5200 Series, PA-3260; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5250, PA-5260, PA-5280; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5250, PA-5260, PA-5280; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
PA-7000 Series, PA-5450, PA-5200 Series, PA-5060, PA-5050,PA-3200 Series PA-3060, PA-850; NOTE: only models or series cited are supported, unlisted models or series are not supported
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
