
Management Features
Safely enabling applications based on users and groups are just a few of the many features that every Palo Alto Networks next-generation firewall supports. A flexible networking foundation facilitates integration into nearly any network. IPsec and SSL VPN deliver enterprise-wide connectivity. Stateful high-availability ensures that your network is always protected.
Policy Control:
Secure Application Enablement
The increased visibility into applications, users and content delivered by Palo Alto Networks simplifies figuring out which applications are traversing your network, who is using them, and the potential security risks. Armed with this data, you can apply secure enablement policies with a range of responses that are more finely tuned than the traditional 'allow or deny' approach.
Balancing protection and enablement with fine-grained policy enforcement
App-ID graphically displays the applications that are traversing your network. It allows you to see who is using applications and the potential security risks. This information empowers you to quickly deploy application-, application function-, and port-based enablement policies in a systematic and controlled manner. Your policies may range from open (allow), to moderate (enabling certain applications or functions, then scan, or shape, schedule, etc.), to closed (deny). Examples may include:
- Allow or deny
- Allow based on schedule, users, or groups
- Apply traffic shaping through QoS
- Allow certain application functions such as file transfer within instant messaging
- Allow, but scan for viruses and other threats
- Decrypt and inspect
- Apply policy-based forwarding
- Any combination of the above
Mixing next-generation policy criteria like applications, application functions, users, groups and regions, with traditional policy criteria such as source, destination and IP address, allows you to deploy the appropriate policy.
Selectively filter applications to quickly create policy control lists
Our application browser allows you to add dynamic application filters to your security policy using a wide range of criteria including:
- Category
- Subcategory
- Underlying technology
- Behavioral characteristic (file transfer capabilities, known vulnerabilities, ability to evade detection, propensity to consume bandwidth, and malware transmission/propagation)
Additional application details you will receive include a description of the application, the commonly used ports, and a summary of the individual application characteristics. Using the application browser allows you to quickly research an application and immediately translate the results into a security policy.
Stop threats and unauthorised file/data transfer
The same levels of fine-grained control that you can apply to a specific set of applications can also be extended to threat prevention. Using a very targeted approach, you can apply:
- Antivirus and antispyware policies to allowed webmail applications
- IPS policies can be applied to Oracle database traffic
- Data filtering profiles can be enabled for file transfer within instant messaging
Traffic shaping ensures business applications are not bandwidth starved
Secure application enablement may entail allowing bandwidth intensive applications such as streaming media. You can strike an appropriate balance by using QoS policies that ensure your business-critical applications are not starved of bandwidth by non-work related applications.
- Guaranteed, maximum and priority bandwidth can be applied across eight traffic queues
- Your policies can be applied to physical interface, IPSec VPN tunnels, applications, users, source, destination and more
- Diffserv marking is supported, enabling application traffic to be controlled by a downstream or upstream networking device
Flexible, policy-based control over web usage
To complement the application visibility and control enabled by our App-ID, you can use URL categories as a match criteria for your policies. Instead of creating policies limited to either 'allow all or block' all behavior, the ability to use URL category as a match criteria permits exception-based behavior. This increases your flexibility and gives you more granular policy enforcement capabilities. Examples of how URL categories can be used in your policy include:
- Identify and allow exceptions to your general security policies for users who may belong to multiple groups within Active Directory (e.g., deny access to malware and hacking sites for all users, yet allow access to users that belong to the security group)
- Allow access to streaming media category, but apply QoS to control your bandwidth consumption
- Prevent file download/upload for URL categories that represent higher risk (e.g., allow access to unknown sites, but prevent upload/download of executable files from unknown sites to limit malware propagation)
- Apply SSL decryption policies that allow encrypted access to finance and shopping categories, but decrypts and inspects traffic to all other categories
Systematically identify and control unknown traffic
Every network has a small amount of unknown traffic. Usually, unknown traffic comes from an internal, custom developed application. In other cases, it is an unidentified commercial application, or, worst case, a threat. Regardless of the amount of unknown traffic, it is a concern for you.
Use the application control features built into Palo Alto Networks next-generation firewalls to systematically identify, investigate and manage unknown traffic on your network in a systematic way. You will notice a dramatic reduction in the risks posed to you by unknown traffic.
Redundancy & Resiliency:
Palo Alto Networks next-generation firewalls support a series of redundancy and resiliency features that ensure your firewall will continue to provide the secure application enablement you need to keep your business running.
Stateful Active/Active or Active/Passive high availability
Active/passive and active/active high availability are supported by our firewalls, complete with session and configuration synchronization. Active/passive high availability supports traditional network designs in which all network traffic passes through a single firewall. Active/active high availability enables application control and threat prevention if you have an asymmetric environment.
- Active/passive: The active device continuously synchronizes its configuration and session information with the identically configured passive device. A heartbeat connection between the two identically configured devices ensures seamless failover if the active device goes down.
- Active/active: Firewalls in an active/active configuration continuously synchronize their configuration and session information. If either device fails, a heartbeat connection signals the other device to take over all of your operations. This ensures session continuity if a device or network fails. To better support asymmetrically routed environments, you can deploy two devices in an HA configuration with either virtual wire interfaces or layer 3 interfaces. App-ID and Content-ID are fully supported in asymmetric environments. Active/active also incorporates flexible layer 3 deployment options supporting load-sharing and interface IP failover.
Built-in resiliency and component redundancy
When your network experiences heavy traffic, our data plane and control plane physically separate to ensure that firewall management access is always available to you, irrespective of your traffic or management load. The data plane houses dedicated processing and memory for networking, security and content inspection; the control plane houses dedicated management processing and memory.
The PA-5000 Series supports several levels of hardware component redundancy:
- Dual hot swappable power supplies
- Dual, solid-state cold swappable hard disk drives
- Single, swappable fan tray
The PA-4000 Series also supports dual hot-swappable power supplies.
Device Management:
Our firewall management philosophy is to make administrative tasks such as report generation, log queries, policy creation, and ACC browsing easy to execute and consistent, no matter which mechanism - web interface, Panorama, CLI or API - you use.
Intuitive and efficient policy management workflow
The familiar look and feel of our policy editor, combined with drag-and-drop objects and rule tagging, will allow you to establish a policy management workflow that suits your administrative processes.
- The policy-browser allows you to quickly create policies that include application, user, and traffic specific threat prevention (IPS, Antivirus, Anti-spyware, etc.), thereby eliminating the duplicate data entry common in other offerings.
- Object drag-and-drop reduces administrative effort by allowing you to reuse the policy objects (users, applications, services or IP addresses) that you have already created.
- Rule tagging allows you to “tag” rules with common names (e.g., DMZ, perimeter, datacenter) so that you can easily search and manage those rules as needed.
Granular control over administrative access
If you have delegated specific sets of tasks to individual staff members, our role-based administration will allow you to designate any of the firewall's features and corresponding capabilities to be fully enabled, read-only or disabled (hidden from view) for specific administrators. For example:
- Your operations staff can be given access to the firewall and networking configuration.
- Your security administrators can be granted control over security policy definition, the log viewer and reporting.
- You can allow key individuals full CLI access, while for others the CLI may be disabled.
All administrative activities are logged so you can see the time of occurrence, the administrator, the management interface used (web interface, CLI, Panorama and the API), and the command or action taken along with the result.
Centralized management of your Palo Alto Networks firewalls
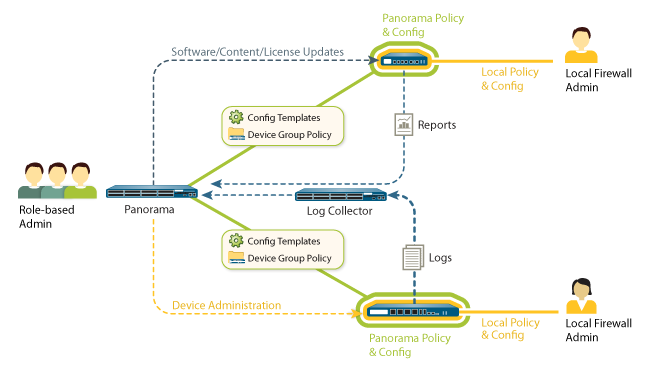
Panorama provides centralized management for multiple Palo Alto Networks next-generation firewalls, enabling you to:
- Browse ACC, view logs, and generate reports across all your firewalls from a central location.
- Use device group and templates to centrally manage your firewall configurations, regardless of location.
- Manage device licenses and updates for software, content, and clients (SSL VPN, GlobalProtect).
By using the same user interface as our individual firewalls, Panorama eliminates the learning curve associated with switching from one mechanism to another. Regardless of the task at hand, the steps you may need to take will be the same.
Industry standard management tools and APIs
A rich set of industry standard management interfaces, combined with a helpful set of APIs, allows you to integrate with existing third-party solutions for superior policy/configuration management, log analysis, reporting and more.
- APIs: A REST management API and a User-ID XML API give you a powerful set of tools to streamline operations and integrate with existing, internally developed applications and repositories.
- Syslog and SNMP v2/3: All logs can be sent to your syslog server for archival and analysis purposes, while SNMP v2/3 support enables integration with a wide range of third-party tools.
- Netflow: Export your IP traffic flow information to a Netflow connector. Separate template records are defined for IPv4, IPv4 with NAT, and IPv6 traffic, while PAN-OS specific fields for App-ID and User-ID can be optionally exported. Netflow integration is not supported on the PA-4000 Series.
In addition to our management interfaces and APIs, the Palo Alto Networks Technology Partner Program makes information available to you on many leading management, reporting and analysis vendors.
Virtual Systems:
Scalable Firewall Services With Virtual Systems
Virtual systems are unique and distinct next-generation firewall instances within a single Palo Alto Networks firewall. Instead of deploying many individual firewalls, security service providers and enterprises can deploy a single pair of firewalls (high availability) and enable a series of virtual firewall instances (virtual systems). Each virtual system is an independent (virtual) firewall within your firewall that is managed separately and cannot be accessed or viewed by other users.
Managed services for customers, business groups, or departments
The flexibility and efficiencies of virtual systems offer security service providers and enterprises very attractive ways to enhance business efficiencies. These include:
- Improved scalability due to fewer devices
- Adding customers
- Lower capital and operational expenditures
Two ways service providers or enterprises use virtual systems is for multi-tenant managed services delivery, or as separate firewall instances within an enterprise network
- Multi-tenant managed services: Within a managed services environment, it's very cost-effective to have a single device support distinct firewall instances. This allows you to deliver security services to multiple customers with just a single device. The breadth of functionality and configuration flexibility we provide lets each customer select from a menu of service offerings, each of which can be enabled and disabled quickly and effectively. Role-based administration allows you to enable your customer to have access to certain functions (such as logging and reporting), while hiding or providing 'read only' (policy editor) access to other functions.
- Departmental services: If you're a large organization, certain technical or compliance requirements may dictate that departmental traffic be protected by a unique firewall instance. On an internal network, a single firewall instance with virtual systems support is extremely cost-effective. Each department can be assigned security services from the 'menu,' and then billed back for those services to demonstrate a return on investment. Just like in a managed services environment, you can allow department staff to have either 'read only' or full access to certain firewall functions while the device is centrally managed by IT.
Protecting network resources through segmentation
Network segmentation is considered to be a network security best practice because it enables your IT department to isolate and more effectively protect critical data. By creating a virtual firewall for a segment of your network, you can protect key content from unapproved access as well as threats and possible data loss. Virtual systems are just one way that you can easily segment your network with Palo Alto Networks.
Granular, role-based administrative control
Each virtual system is a self-contained, fully operational Palo Alto Networks firewall, complete with separate management interfaces. This ensures that other customers or departments can only see or modify their own policies. Within each virtual system, role-based administrative access control allows you to delegate feature-level administrative access (enabled, read-only, or disabled and hidden from view) to different staff. Using role-based administration, service providers can build a menu of services to selectively enable, while enterprises can delegate access to key individuals as needed.
Centralized Management:
The centralized management features in Panorama will minimize the administrative efforts and operational costs associated with your deployment of our next-generation firewalls in multiple locations - either internally or globally. Panorama allows your team to centrally manage all device aspects including configuration and policy deployment, visibility into applications, users and content as well as logging and reporting.
Global device management
Using a combination of Device Groups and Templates, your team can quickly configure one of our firewalls remotely and then deploy new or updated global policies that co-exist with local policies. The combination of global and local policies allows you to ensure compliance with internal or regulatory requirements, while local device rules maintain both security and flexibility. Granular role-based administration complements shared-policies by allowing you to assign specific tasks to different members of your team, thereby ensuring appropriate separation of roles and responsibilities.
Centralized visibility, logging and reporting
With the same look and feel as the web interface, Panorama gives you visibility into the applications, users and content traversing your devices along with granular logging and reporting - all at both a global or individual device level.
- Visibility: With the same look and feel as the web interface, Application Command and Control (ACC) in Panorama gives you a global or individual device view into the applications, users and content traversing your network. The end result is that you will know more about the traffic and activity on your network and can make more informed security policy decisions.
- Logging: For either an individual device, or all devices, Panorama administrators can quickly view log activities using dynamic log filtering by clicking on a cell value and/or using the expression builder to define the filter criteria. Results can be saved for future queries or exported for further analysis.
- Log Forwarding: Panorama can aggregate logs collected from all your Palo Alto Networks firewalls, both physical and virtual form factor, and forward them to a remote destination for purposes such as long term storage, forensics or compliance reporting. Panorama can forward all or selected logs, SNMP traps, and email notifications to a remote logging destination such as a Syslog Server (over UDP, TCP or SSL).
- Reporting: Predefined reports can be used as-is, customized, or grouped together as one report to suit specific requirements. In addition to ad hoc reporting, custom and predefined reports can be scheduled and exported in a variety of formats.
Software, Content and Licensing Management
Panorama allows you to take the systematic approach of first qualifying a change to the firewall in a controlled environment, then delivering it to the production firewalls. From a centralized location, you can manage software updates, content (application updates, antivirus signatures, threat signatures, URL filtering database, etc.) and firewall licenses.
Logging and Reporting:
Traffic Monitoring: Logging, Reporting, and Forensic Analysis
Security best practices dictate that you strike a balance between being proactive, continually learning and adapting to protect your corporate assets, and being reactive and investigating, analyzing and reporting on security incidents. ACC and the policy editor allow you to proactively deploy application enablement policies, while a rich set of monitoring and reporting tools enable you to analyze and report on the applications, users and content traversing your network.
Real-time traffic analysis and forensics
Our firewall maintains logs for WildFire, configurations, system, alarms, traffic flows, threats, URL filtering, data filtering, and Host Information Profile (HIP) matches. You can quickly analyze network activity by clicking on a cell value and adding multiple criteria using the expression builder - the results can be stored for future use or exported to CSV for additional analysis. In addition, all logs can be sent to a syslog server for analysis by a wide range of third party solutions.
Fully customizable reporting
Available as a standard feature, our reporting features allow you to generate informative reports using 40+ predefined reports, or by using report builder, which lets you assemble a fully customized report that can be saved, exported to PDF/CSV or XML and scheduled to run, and then be emailed. A few of the standard reports include:
- Behavioral botnet report: Data regarding unknown applications, IRC traffic, malware sites, dynamic DNS, and newly created domains is analyzed with the results displaying a list of potentially infected hosts that can be investigated as members of a botnet.
- PDF Summary report: A fully customizable one-page summary report that includes data for the top five in each category as well as trend charts that are not available in other reports.
- User-activity report: Allows you to generate a time-based report that shows application and web browsing activity for specific users.
- App-Scope: Complementing the real-time view of applications and content provided by ACC, App-scope provides a dynamic, user-customizable view of application, traffic and threat activity over time.
Integration with Security Event and Incident Management (SIEM) tools
Our firewall allows you to send all the logs to a syslog server for archival and analysis purposes. In addition, we have a wide range of proven technology partnerships with nearly all of the SEIM vendors.

